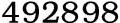|
The Case of the Computer That Got Lost The stories are true; the names and places have been changed to protect the potentially guilty. A few years ago, Debby Johnson, an attorney from a large firm based in Kansas City, contacted me about a relatively simple matter. I was to travel to offices in Sacramento from my San Francisco-area labs, copy a computer's disk drive, and locate emails sent by the plaintiff to his brothers and sisters, of which he had nine. The case was a product liability lawsuit for an amount in the tens of millions of dollars. The plaintiff claimed that his health had been damaged by an international firm's defective product, although he was symptom-free at the moment. What was the product? Let's say it was coffee. From the cool Bay Area in summer, I traveled to downtown Sacramento, where it was a balmy 106 degrees. I knew I was sweating, but inside I was cool. I wondered if someone else would be in hot water soon. It is not unusual for me to never meet my client, for computers can be shipped to me at my lab, but Debby was there in the law offices of the plaintiff's attorney. In an oak-paneled conference room we met with counsel for "the other side" and with the plaintiff himself. He sat smugly with his shiny computer on the conference table, friendly enough in spite of his contention that I would never find the offending emails he had allegedly sent years before. My client believed that this fellow had sent emails to his siblings that would disprove his contention - that would show him to be making up a case to snag a cool few ten millions. I removed the hard disk from our man's system to make a forensic copy to work with and analyze. I was surprised to find that the hard disk was 100GB in size. A drive of that capacity was fairly new and unusual to see in a case this soon after it had come on the market. I was prepared for a much smaller disk drive, as I had been told I'd be seeing one about 20% the size. Fortunately, there was an electronics superstore nearby, so I doffed my suit jacket, cranked up the air conditioning on my minivan / lab wagon (that beauty just turned over 200,000 miles on the day I'm writing this), and headed on over for a bit of new gear. Forty-five minutes and a bit of melted rubber later I arrived back at the scene to forensically clean the new disk drive by writing zeroes to every sector.. Once cleared to my satisfaction, I set up the copy process. In those days, while I was partial to Diskology's Disk Jockey, the version I had then didn't seem to be able to handle what was such a large drive for the time. I probably used Byte Back on a forensic Intel box I had brought just in case. I began the copy process and it went without a hitch. But while the copy was proceeding, I began to wonder - wasn't this a pretty big drive to have been around at the time of the alleged emails? And for that matter, wasn't this computer pretty fast for its age. And did Windows XP really come on the market before these emails were to have been written? I was beginning to suspect that the game was rigged, and that I never would find the plaintiff's deleted emails on that computer. I discussed the matter with Debby. I guessed that the plaintiff was right about the task being futile - because I guessed that the offending emails were never on this computer. I said I'd be willing to look for them, but I didn't want to waste my client's cash. Debby asked me to look into the matter of the components' age when I got back to HQ. A few inquiries with the manufacturer and a couple of Google searches later, I was pretty well convinced that the fellow had never written those emails on this computer. Windows XP was almost too new, the disk drive was a couple of weeks too modern, and the computer was a month or two younger than those emails. Debby called opposing counsel - who had no idea why this might not be the original system…until he checked with his man. Turns out he had "set it on the curb for trash pickup" because it "wasn't working." The attorneys weren't happy. The court wasn't happy. The only solution was for me to go to the nine brothers and sisters in four states to copy their personal computers and sift through those for the offending emails. Do you think they were happy to hear from me? Would you be if your brother put you on the spot like that? Each of them had to agree that a perfect stranger - one who was working against their beloved brother - could come into their homes and look through everything on their personal computers. The most telling example of their displeasure was from one brother, a former Viet Name-era Green Beret, who - in response to my phone call asking when would be a good time to show up - said "I didn't spend two years marching up and down the God**m Ho Chi Minh Trail for this s**t!" I understood. It turns out that opposing counsel had never gotten around to telling this group that a computer forensics guy would be calling them and they needed to cooperate. I found that out when I told Debby of the righteous resistance I had come up against. She straightened it out with counsel and the next set of phone calls I made to the sibs was a lot more congenial. The next several days, traveling from state to state, town to town, brother to sister to brother and on and on to copy the private data of nine innocent family members had its challenges. But that's a story unto itself…I'll spare you most of the details. Upon my return, the protocol called for me to search all of the data for any correspondence from - let's call him "The Brother" that referenced his struggles with … we're calling it Coffee. I was then to print out the references I found, and send a copy both to the judge and to opposing counsel for privilege and relevance review. Debby and her firm were not to get a look at the data until anything either private or irrelevant had been picked out, and only the remainder produced. What did I find? Around the time of the alleged emails, lo and behold, I found actual emails. The whole family was talking about The Brother's struggle with Coffee, their individual investigations into Coffee, and the upcoming lawsuit about Coffee. At one point, one email pointed out that this guy Burgess was going to be looking into everyone's email, and wouldn't it make sense not to talk about Coffee? They agreed. They now spoke only of … "the C-Word." What else did I find when I performed my electronic discovery and digital forensic analysis? Well, for the most part, I just can't talk about it. There are some things on your computer you wouldn't want me talking about, I'm sure. There are things on my computer I wouldn't want me talking about either! E-discovery often has to be a pretty private process. But there was one particularly interesting finding. When I called the Green Beret Brother (GBB) from his sister's place across town, and asked for permission to head on over to make the copy of his computer, he obligingly told me it was okay. When I got there, he first asked me to read and sign a statement that I wouldn't hold him liable for any damage to me or my equipment - unintentional or otherwise. Well that was a little scary coming from a guy trained in the arts of stealth, war, and undoubtedly the garrote. But as the paper didn't seem like a legal document, I signed it, if that was what would get me in to do my work. He was pleasant enough, the music he had on was good, and the copy went without a hitch. And I left alive and undamaged - a plus, indeed! Once in my lab, I discovered the last thing that had happened on his computer. About one minute after my phone call for permission to go over, GBB had sent himself an email and then immediately deleted it. The subject, all in caps, was "COFFEE!" No "C-Word" fooling around for him. The message in the body was simple and succinct: "If you find this email, F*** YOU!!!!!" It's nice when a person knows how he feels and is able to express it freely. There was also a deleted photograph attached to the deleted email. Upon recovering same, it turned out to be a very recent photo of an extended middle finger - presumably GBB's finger. Visual aids are always helpful in understanding the subject matter, don't you think? In the end, I produced about 75 pages of documentation I thought relevant. Of course, I had to include GBB's missive. As expected opposing counsel called everything irrelevant or privileged. Also as expected, the judge allowed all of the documents I had produced - with a number of lines redacted - to be delivered to my client. Everyone's favorite was the literate bit produced by GBB. As for The Brother - the court decided that not only was he not very honest, due to the destruction of the most important data in the case - his original computer - but the evidence and the relevant emails showed him to be apparently undamaged by the Coffee. The case went to defeat, Debby and her firm were happy, and GBB became a legend. This is just one of the many "CSI* - Computer Forensics Files: Real Cases from Burgess Forensics". Stay tuned for more stories of deceit uncovered by computer forensics. *The Free Dictionary lists more than 160 definitions for CSI at acronyms.thefreedictionary.com. We choose Computer Scene Investigation. Steve Burgess is a freelance technology writer, a practicing computer forensics specialist as the principal of Burgess Forensics, a highly regarded expert witness, and a contributor to the just-released Scientific Evidence in Civil and Criminal Cases, 5th Edition by Moenssens, et al. Mr. Burgess may be reached at http://www.burgessforensics.com - email: steve@burgessforensics.com
Related Articles -
computer forensics, electronic discovery, deleted email, data recovery, law, digital discovery,
|